What is CSEc Peripheral
console.log( 'Code is Poetry' );
CSEc is a microcontroller peripheral in NXP Semiconductors S32K1 series of Automotive MCU’s. CSEc peripheral is a security subsystem, which is based on SHE standard for doing cryptographic operation and establishing secure communication between the ECUs in the car.
Security subsystem is a dedicated subsystem within an IC (Microcontroller or SoC) through which we can perform cryptographic operations in microcontroller and protect cryptographic keys from the software attacks.
Broadly there are 2 types of security sub-systems in a microcontroller for doing cryptography operations:
- Secure Hardware Extension (SHE)
- Hardware Security Module (HSM)
The security-subsystem, which we are discussing in this blog: CSEc Module, is based on SHE standard security sub-system. That means using the CSEc peripheral present in S32K144 MCU, we can perform symmetric crypto operations and secure up to 17 user keys.
To know more about the SHE standard, refer to this blog.
Configuration of CSEc peripheral
As CSEc peripheral is SHE standard based security-subsystem and in SHE standard all the controlling of the crypto algorithms and operation’s is done via finite state machine or small CPU core.
In S32K1 series, it is done via finite state machine thus the control logic for using CSEc peripheral is command wise. There are commands specified for doing crypto operations according to HIS-SHE specification version 1.1 We just need to specify which command to send, and corresponding crypto operations are executed. (make a graphic showing state machine, she specification and commands with elecronicsv2 and s32k144 photo)

The state machine algorithm to use CSEc peripheral is implemented in FTFC module of the S32K1 MCU’s. FTFC is a Flash memory module which is a Hardware IP in S32K1 series of MCU which is used to modify flash memory contents. Flash memory configuration, initialization and all other things are done by FTFC module. Will deep dive into FTFC module in separate blog.
For now, to use CSEc peripheral, features have been added to the FTFC module to support SHE functional specification version 1.1. The FTFC module enables encryption, decryption, CMAC generation-verification and algorithms for secure messaging applications. Additional APIs are also available for Secure Boot configuration, True Random Number Generation (TRNG) and Miyaguchi-Prenell compression. The FTFC core takes care of the flash as well as CSEc functionalities.
So, to use CSEc peripheral, we need to configure FTFC module. This configuration is flash memory partitioning, we need to partion the flash memory to emulated EEPROM. By doing so, the FTFC module enables encryption, decryption and CMAC generation-verification algorithms for secure messaging applications. The user can configure the FTFC module for emulated-EEPROM operation by issuing a Program Partition Command (PRGPART). The PRGPART command provides flexibility to specify the partition size between emulated-EEPROM operation and normal operations as per user’s wish.
To enable CSEc functionality, the device must be configured for emulated-EEPROM operation. The PRGPART command is used to enable CSEc and also provides a mechanism to specify the key size. Depending on the key size, the last 128/256/512 bytes of EEERAM are reduced from the emulated- EEPROM and become un addressable (so as corresponding EEPROM –backup). This storage is secured and utilized to store cryptographic keys.
Once the user configures the FTFC module for CSEc functionality and loads the user keys for the security operations, the device is ready for any security related operations as described in the HIS-SHE specifications.
//Show practical codes/API and working of flash memeory partionining
// understand abput how memory configuration is being done, what size is done and what size is left and which API is used
//How to check CSEc peripheral is configured and memory partioning is done.
Crypto operation command using CSEc
Okay so now once CSEc is being configured and initialized for use now let’s dwell into how to do crypto operations with it.
CSEc peripheral uses command-based programming interface. Crypto operations like Encryption, decryption, loading keys, generating keys and etc. all are done via commands. These commands are handled by CSEc PRAM interface.
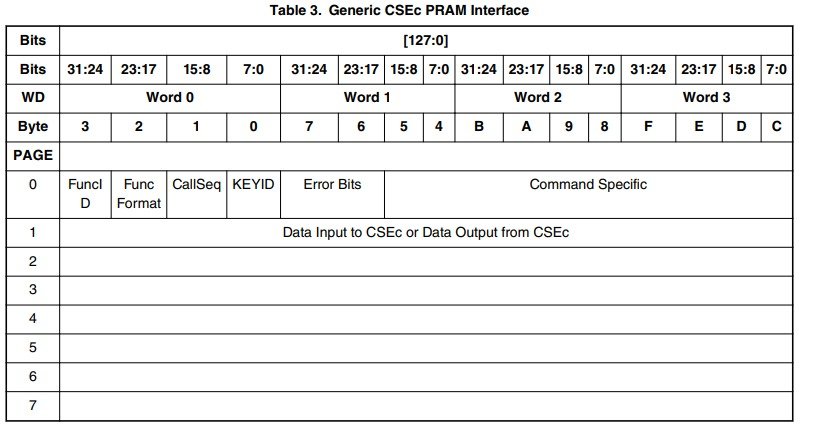
CSEc PRAM interface is a memory area of around 128 bytes. which is divided into 8 sections. Each section is termed as page here. Starting from page 0 to page 7. Each page of 16 bytes. As shown in below pic.
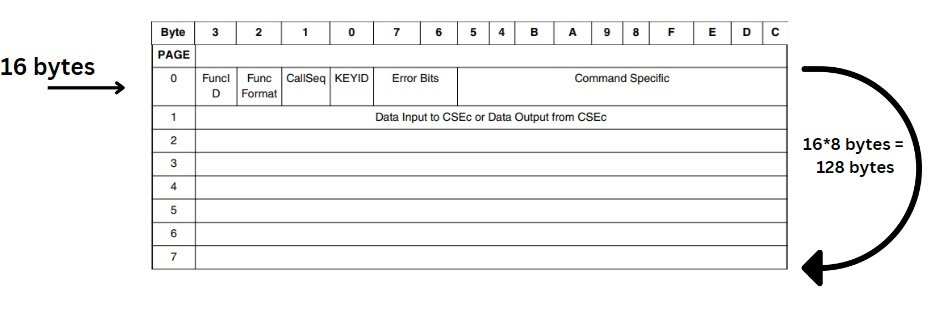
So, we send the command by writing it on page 0 according to the command header specified below and with the command some additional information required by that command and in return we get the result on pages 1-7.
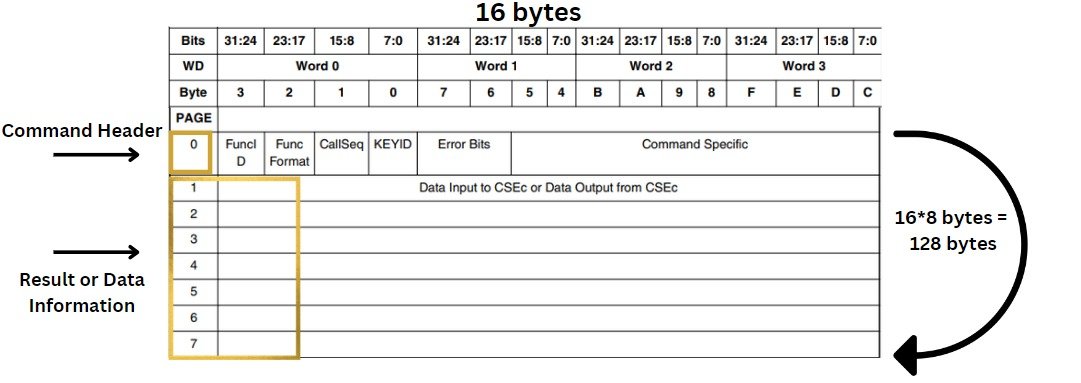
The Structure of the command header is standard for all the commands, command header is divided into 6 bytes.
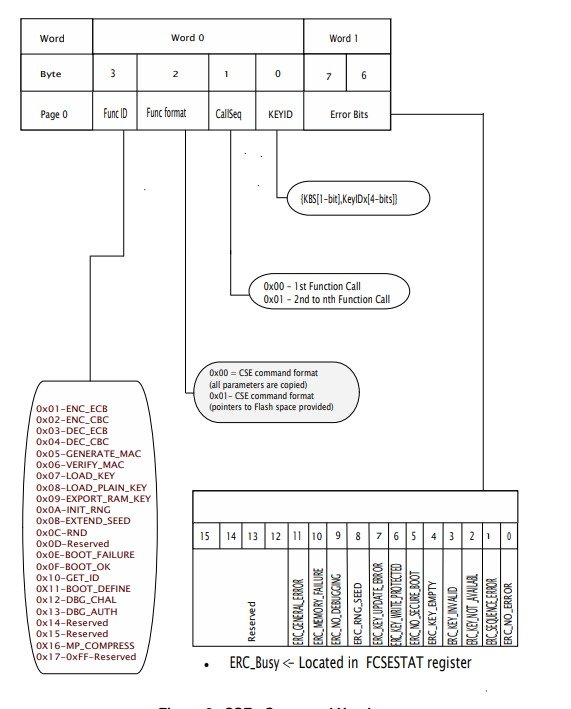
–> FuncID: Function Identification (ID) field is a 1 bit long and specifies the security command to be executed. Valid from 0x00 to 0x16. In the code enum
One can relate CSEc PRAM interface as a Sheet. That sheet is divided into 8 horizontal lines are. Terminologies to refer to these lines is pages. So their are total 8 pages, starting from page 0 to page 7.
Now in first page 0, we write the command
In the above image, first page Page 0, includes the command header (Page 0, Word 0) and message control length (Page 0, Word 3). The rest of the pages are utilized for input/output data information.
Writing to the command header triggers the macro to lock the CSEc PRAM interface and start the CSEc operation. Hence, to setup a CSEc command, the user should first enter data information followed by message length information and must write command header last.
Cryptographic Keys in CSEc
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Cryptographic ciphers in CSEc
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Cryptographic Operations in CSEc
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Features of CSEc Peripheral
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
CSEc Peripheral has following features:
- Comes under, EVITA-Light HSM and SHE specification/requirement.
- AES128 encryption/decryption.
- AES-CBC and ECB mode supported.
- CMAC generation and verification using AES-128 cipher.
- True and Pseudo-random number generator.
- Miyaguchi-Preneel compression Function for Key Derivation.
- 24 Kilo Bytes of Secure Memory for Firmware and Keys.
- 17x General Purpose/User keys and 5 Special purpose keys, in total 20+ crypto keys can be stored/managed via the CSEc module.
- Secure Boot is supported for sequential, parallel, and strict mode configurations.
CSEc Peripheral Theory in S32K144 MCU
Advantages of CSEc security-subsystem
- To secure automotive applications and products.
- To prevent hacking and intruder engagement in real time automotive applications
- Greak for students to do hands-on and learn cryptographic operations in embedded. As cybersecurity is increasing day by dad.
Practical use cases/projects that can be built using Crytography with ElecronicsV2
These cryptographic capabilities in S32K144 Microcontroller and using ElecronicsV2 board for it, makes the ElecronicsV2 suitable for applications like:
- Secure Milage:
- Electronic Immobilizers
- Component protection
- Flash programming and firmware update
- Secure communication(CAN-LIN network)
- Vehicle to vehicle communication for ADAS and Smart vehicles.
(To read bit about these applications and give one-liners for that)
CSEc Peripheral SDK in S32K144 MCU
CSEc Peripheral Demo Code's
1) csec_keyconfig_s32k144
This demo